Certified Cybersecurity Technician v1 (CCT)
Completed
Certified Cybersecurity Technician v1
Course Prerequisites
Certainly! To successfully undertake the Certified Cybersecurity Technician (C|CT) course, it is recommended that students possess the following minimum prerequisites:
- Basic knowledge of networking concepts, including understanding of the OSI model, IP addressing, and common networking protocols such as TCP/IP.
- Familiarity with computer operating systems, particularly Windows and Linux, since many of the security concepts will apply to these platforms.
- Understanding of core cybersecurity principles, such as confidentiality, integrity, and availability (CIA triad).
- Awareness of common cybersecurity threats and vulnerabilities, which will be built upon throughout the course.
- Some experience with using computers and navigating the internet securely is beneficial.
- Willingness to learn and engage with hands-on labs and technical content.
Please note that while prior experience in IT or cybersecurity is helpful, it is not strictly necessary. The C|CT course is designed to provide foundational cybersecurity skills and knowledge, making it suitable for individuals who are new to the field but have a strong interest in pursuing a career in cybersecurity.
Road Maps
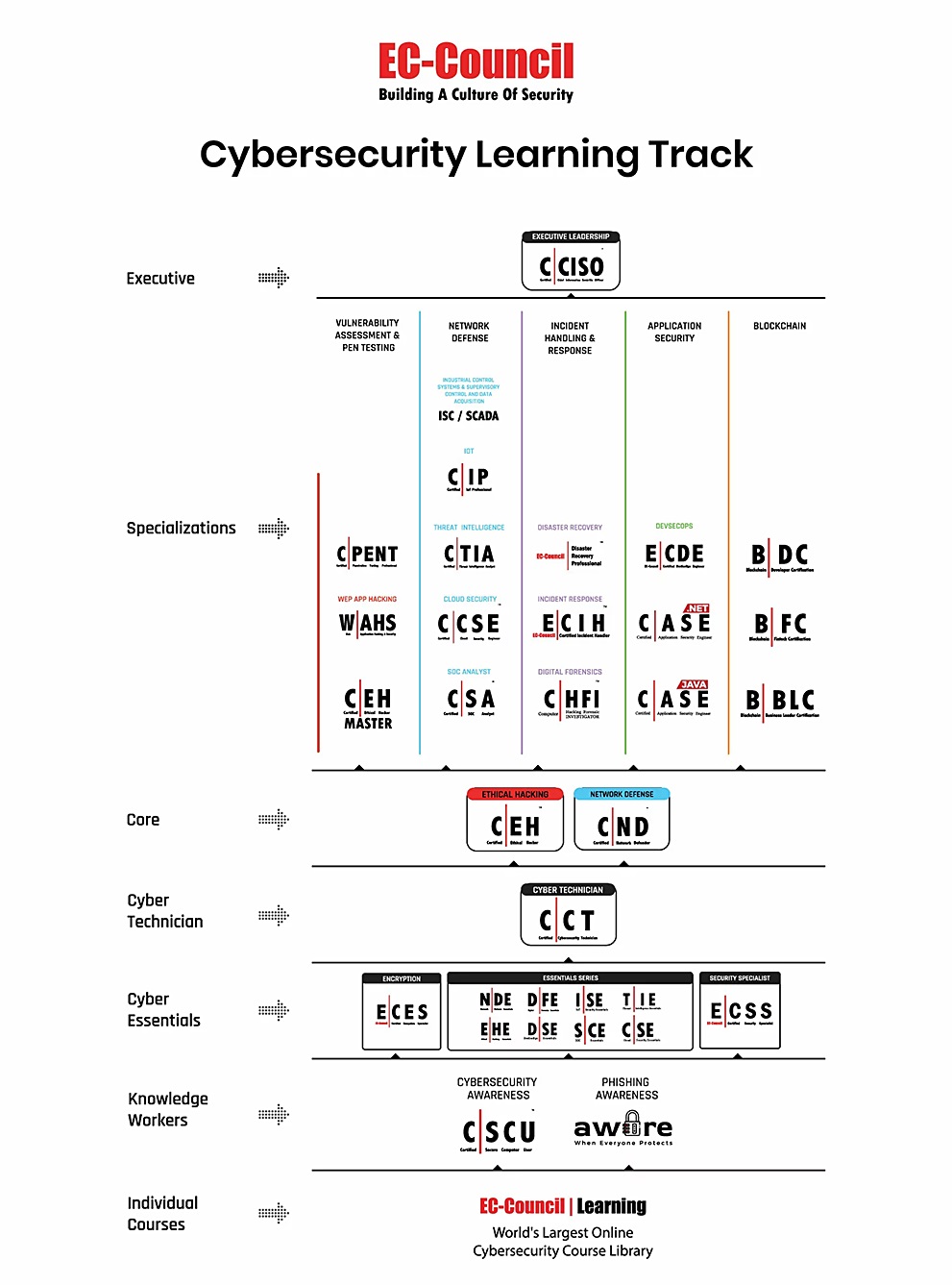
The Certified Cybersecurity Technician (C|CT) course is designed for IT professionals seeking to enhance their security expertise.
Target audience for the Certified Cybersecurity Technician (C|CT) course includes:
- Entry-level cybersecurity technicians
- Network administrators seeking cybersecurity skills
- IT professionals wanting to transition into cybersecurity roles
- Helpdesk technicians aiming to specialize in security
- System administrators looking to strengthen security practices
- Recent graduates from IT programs focusing on security
- Cybersecurity enthusiasts with a foundational IT background
- IT staff in government or defense services requiring security expertise
- Professionals responsible for implementing security controls and protocols
- Security consultants seeking to update their technical skills
- Professionals preparing for cybersecurity certification exams
- Employees of organizations aiming to comply with cybersecurity regulations
- Technical support engineers expanding their knowledge in network security
- Incident responders and computer forensics analysts
- Risk management professionals looking to understand technical controls
- Business continuity and disaster recovery planners with a focus on IT security
- Professionals working with IoT, OT, or mobile security
- Individuals responsible for securing virtualization and cloud environments
Learning Objectives - What you will Learn in this Certified Cybersecurity Technician(C|CT)?
Introduction to the Course's Learning Outcomes and Concepts:
The Certified Cybersecurity Technician (C|CT) course equips learners with a comprehensive understanding of cybersecurity principles, techniques for securing networks and systems, and best practices for incident response and risk management.
Learning Objectives and Outcomes:
- Understand information security threats and vulnerabilities to identify potential risks to organizations.
- Recognize various information security attacks and the methodologies used by cybercriminals.
- Grasp the fundamentals of network security, including the design and implementation of secure network architectures.
- Learn about identification, authentication, and authorization mechanisms to manage access to information and resources.
- Implement administrative controls to establish a robust security policy and governance framework.
- Apply physical controls to protect organizational assets from physical threats and ensure environmental security.
- Deploy technical controls to safeguard information systems through encryption, firewalls, intrusion detection systems, and more.
- Utilize network security assessment tools and techniques to identify vulnerabilities and assess risks within the network.
- Address application security issues, focusing on securing software applications against exploitation.
- Understand the security challenges and best practices related to virtualization, cloud computing, and wireless networks.
- Secure mobile devices and understand the unique threats posed to mobile platforms.
- Protect Internet of Things (IoT) and Operational Technology (OT) devices against emerging security threats.
- Apply cryptography to ensure confidentiality, integrity, and authentication of data.
- Ensure data security through effective data protection strategies and compliance with data privacy regulations.
- Develop troubleshooting skills to quickly resolve network issues while maintaining security posture.
- Monitor network traffic and analyze logs to detect suspicious activities and potential security breaches.
- Prepare for and respond to cybersecurity incidents with a structured incident response plan.
- Conduct computer forensics investigations to extract evidence and understand the scope of a security incident.
- Plan and implement business continuity and disaster recovery strategies to minimize downtime and data loss.
- Apply risk management principles to identify, assess, and mitigate cybersecurity risks effectively.
Commenting is not enabled on this course.