%20?unique=130aebf)
Certified Chief Information Security Officer v3 (CCISO)
| Responsible | Techventurz |
|---|---|
| Last Update | 08/04/2025 |
| Members | 2 |
CCISO

Certified Chief Information Security Officer v3
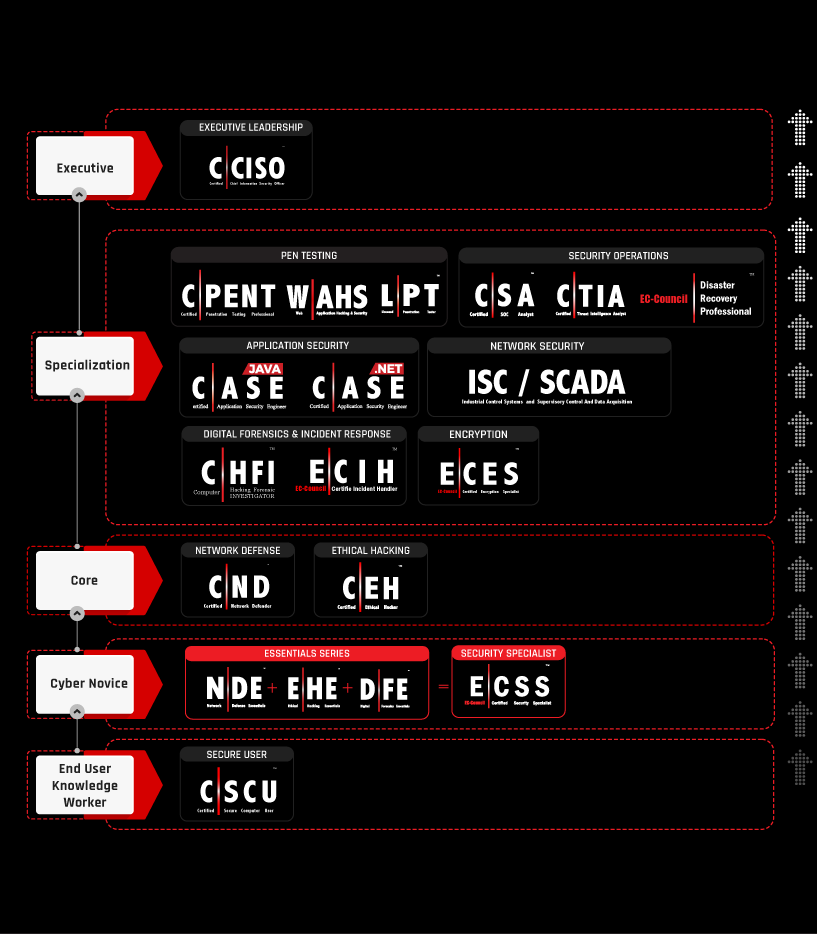
Road Maps

Target Audience for Certified Chief Information Security Officer( CCISO )
The Certified Chief Information Security Officer (CCISO) course is designed for senior-level information security executives.
- Current Chief Information Security Officers (CISOs)
- Vice Presidents of Information Security / Cybersecurity
- Information Security Directors / Managers
- Information Technology Directors / Managers responsible for IT security
- Chief Information Officers (CIOs) involved in information security governance
- Senior IT professionals aspiring to be CISOs
- Information Security Consultants and Advisors
- Senior Information Security Auditors
- Information Security Analysts / Engineers with management aspirations
- IT Risk Management Professionals
- IT Governance Professionals
- Compliance Officers dealing with information security requirements
- IT/Information Security Leaders in charge of strategic planning
- Information Security Incident Responders with senior management roles
- Network Architects and Planners focusing on security infrastructure
- Information Security Policy Makers
- Senior System and Network Administrators
- Information Security Training Professionals
- Senior members of IT/Information Security law enforcement agencies
- Entrepreneurs looking to gain knowledge in information security management
Learning Objectives - What you will Learn in this Certified Chief Information Security Officer( CCISO )?
Introduction to the CCISO Course Learning Outcomes:
The CCISO course is designed to equip information security leaders with the most effective and efficient strategies for defending organizational cyber environments.
Learning Objectives and Outcomes:
- Develop and manage an information security governance program aligning with organizational goals and compliance requirements.
- Understand and apply information security management and control frameworks, standards, and best practices including ISO 27000 series and FIPS.
- Design and implement a comprehensive risk management program, identifying and mitigating risks while understanding acceptable risk levels.
- Establish and maintain a disaster recovery and business continuity strategy that supports organizational resilience.
- Develop and oversee a strategic plan for information security, integrated with business objectives and financial planning.
- Manage and audit information systems controls to ensure integrity, confidentiality, and availability of information assets.
- Lead information security projects effectively, ensuring they meet organizational objectives, budget, and timelines.
- Gain proficiency in core information security competencies such as access control, network defense, and encryption technologies.
- Conduct vulnerability assessments and penetration testing to identify security weaknesses and oversee the implementation of corrective measures.
- Oversee computer forensics and incident response, ensuring proper handling of security incidents and legal compliance.

Certified Chief Information Security Officer v3

Preview
Road Maps

Target Audience for Certified Chief Information Security Officer( CCISO )
The Certified Chief Information Security Officer (CCISO) course is designed for senior-level information security executives.
- Current Chief Information Security Officers (CISOs)
- Vice Presidents of Information Security / Cybersecurity
- Information Security Directors / Managers
- Information Technology Directors / Managers responsible for IT security
- Chief Information Officers (CIOs) involved in information security governance
- Senior IT professionals aspiring to be CISOs
- Information Security Consultants and Advisors
- Senior Information Security Auditors
- Information Security Analysts / Engineers with management aspirations
- IT Risk Management Professionals
- IT Governance Professionals
- Compliance Officers dealing with information security requirements
- IT/Information Security Leaders in charge of strategic planning
- Information Security Incident Responders with senior management roles
- Network Architects and Planners focusing on security infrastructure
- Information Security Policy Makers
- Senior System and Network Administrators
- Information Security Training Professionals
- Senior members of IT/Information Security law enforcement agencies
- Entrepreneurs looking to gain knowledge in information security management
Learning Objectives - What you will Learn in this Certified Chief Information Security Officer( CCISO )?
Introduction to the CCISO Course Learning Outcomes:
The CCISO course is designed to equip information security leaders with the most effective and efficient strategies for defending organizational cyber environments.
Learning Objectives and Outcomes:
- Develop and manage an information security governance program aligning with organizational goals and compliance requirements.
- Understand and apply information security management and control frameworks, standards, and best practices including ISO 27000 series and FIPS.
- Design and implement a comprehensive risk management program, identifying and mitigating risks while understanding acceptable risk levels.
- Establish and maintain a disaster recovery and business continuity strategy that supports organizational resilience.
- Develop and oversee a strategic plan for information security, integrated with business objectives and financial planning.
- Manage and audit information systems controls to ensure integrity, confidentiality, and availability of information assets.
- Lead information security projects effectively, ensuring they meet organizational objectives, budget, and timelines.
- Gain proficiency in core information security competencies such as access control, network defense, and encryption technologies.
- Conduct vulnerability assessments and penetration testing to identify security weaknesses and oversee the implementation of corrective measures.
- Oversee computer forensics and incident response, ensuring proper handling of security incidents and legal compliance.
00:00
0
0